Yesterday, I posted an article on starting to work with application permissions against Microsoft Graph when using the Power Platform. Today we’re going to look at how to make requests towards the Microsoft Graph API when working with application permissions in contrast to the previous posts in this series on making requests when working with delegated permissions.
Whilst this is more simple than working with delegated permissions more often than not, remember when it is appropriate to use application permissions, and when we shouldn’t. If you’re not sure when to use application permissions, or what they do and grant access to, it is important to review the following content prior to continuing with this guide.
If you’ve been enjoying the content in this series, make sure you subscribe to my blog to continue to get my posts directly in your inbox. 📩
SubscribeWorking with the HTTP step
So to make requests to Microsoft Graph using application permissions, we simply need to use a single HTTP step to call the API and carry out the operations we wish to.
Simply take the operation you’d like to carry out, and the request you’d like to make and populate a HTTP action with the relevant content such as a request URL, method, headers and body. Then we will work on authentication.
If you’re not sure what type of request you’d like to make yet, and you’re just starting to get to grips with Microsoft Graph, I recommend going back to the start of this series on Microsoft Graph and utilising the wider Microsoft Cloud ecosystem when building on the Power Platform.
Building a request and handling authentication
Let’s say for example I want to read all devices and get this data from Microsoft Graph without a user present because I’m working in a scenario where this is for automation without user interaction. I’m going to add the Device.Read.All application permission to my app registration and then compose the following request in a HTTP step in my flow.
Method: GET
URI: https://graph.microsoft.com/v1.0/devices
Headers: Content-type application/json
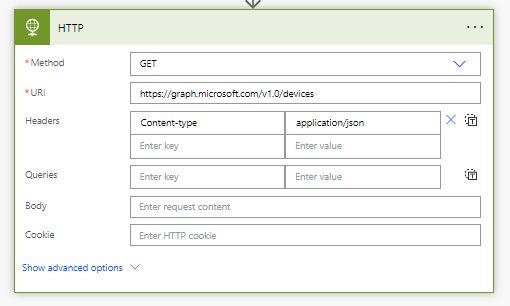
Now I’m going to expand the advanced options on the step and work on authentication.
First I’m going to set the authentication type to Active Directory OAuth
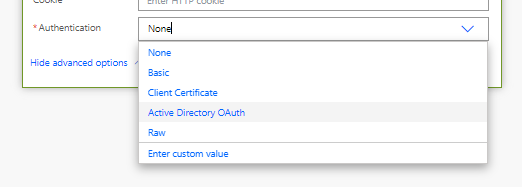
Next I’ll set the following fields.
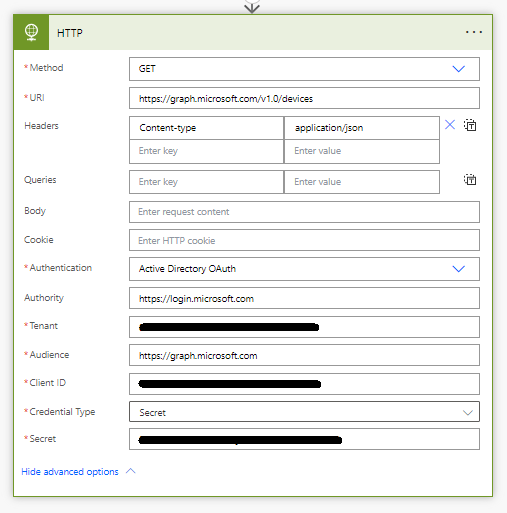
Authority: https://login.microsoft.com
Tenant: Tenant ID which can be found on your app registration overview
Audience: https://graph.microsoft.com
Client ID: The identifier for your app registration which can be found on the app overview.
Credential type: Secret
Secret: Paste in the secret value you copied from your app registration in the previous post in this series. Preferably use Azure Key Vault to populate the value here dynamically also utilising secure inputs and outputs around flow steps.
If you haven’t worked with Azure Key Vault before, follow the guidance in this post.
Your flow action should now be looking a little bit more like this
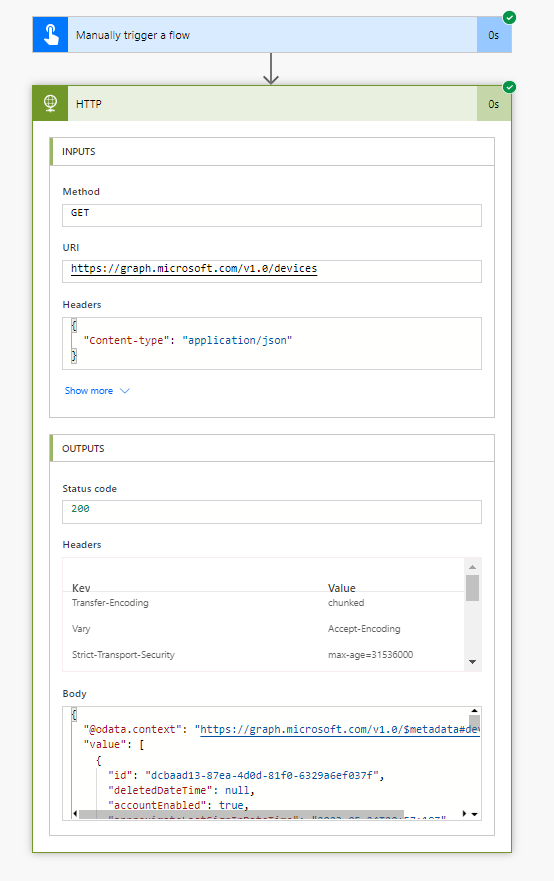
Now give your flow a test and you should see data coming back. Now we’re utilising application permissions to make an application only call towards Microsoft Graph! I will mention again though that you should exercise caution when using this approach and only use it where you absolutely need to. Make sure you’ve read the previous posts in this series to understand when this is the approach to take.
In my next post, we’ll look at using application permissions when working with Power Apps, taking the data we’ve retrieved using a HTTP step in a flow, into an app to display in a front end.
If you’re enjoying the content in this series, make sure you subscribe to my blog to continue to get my posts directly in your inbox. 📩

