In this blog post, we’ll start to move onto working with application permissions against Microsoft Graph, when we might use application permissions, and the approaches we can take to utilising them in our Power Platform solutions when necessary.
If you’re enjoying this series on Microsoft Graph, and want my posts to land in your inbox as soon as they’re published, make sure you subscribe to my blog below!
SubscribeTaking a step back…
Before we continue to look at the approaches we can take to utilising application permissions against Microsoft Graph when working with the Power Platform, let’s discuss what these do, what they give access to, and when we’d need to use them.
Effectively application permissions, allow you to authorise against resources through an Azure AD secured API such as Microsoft Graph without the need to have a users context or a ‘user’ present. This means we only need the application present for authorisation against resources. This is the approach needed for cases where a service might run without a user present for example, or when an application acts on its own.
We might use application permissions for cases such as automation and backup, as opposed to examples such as a user interacting with an application that has a front end.
We would also need to use this approach when the data were attempting to interact with can’t be scoped to a single user in terms of permissions and access control.
We shouldn’t use application permissions, if a user is present when the interaction with the API needs to be made, and the data or resources can have access scoped to a single user or multiple users. Scenarios where a user is present and resources can be scoped to a single user or multiple users should use delegated permissions for access to be least privileged.
Configuring an app registration with application permissions
Now that we’ve recapped on when application permissions are suitable to be used, and when you shouldn’t use them, lets focus on how we can configure authorisation for an application to make application only calls with application permissions.
Start by creating an application by following this guide…
When creating your app registration, in contrast to an application for working with delegated permissions and something like a custom connector for example, you won’t need to set a redirect URI.
Once you’ve created your app, you’ll need to add the relevant application permissions for what you’d like to retrieve from Microsoft Graph without the context of a user present.
Do this by heading to the API permissions section of your app registration, then select add a permission. Following this select the Microsoft Graph API. Then select application permissions to see the application permissions you can add to your application.
Tick the permissions you need to add to your app to interact with the API for your desired solution. Then select add permissions.
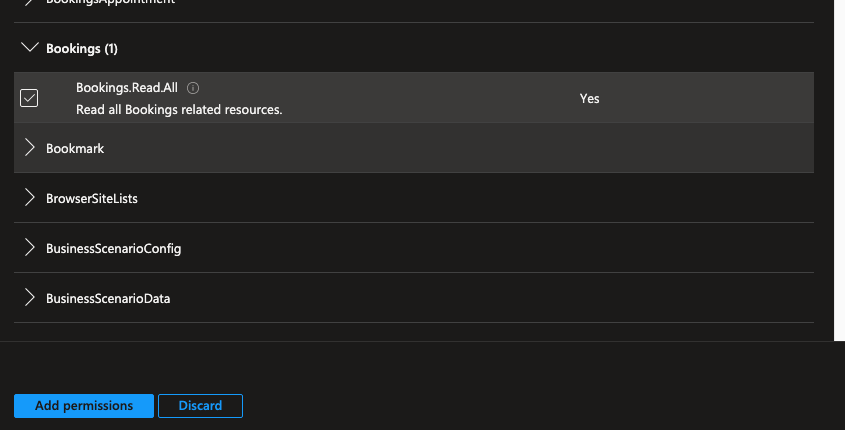
Now you’ll need to have admin consent granted by a global administrator for the tenant. Application permissions grant access to all of the resources for the permission category you’re working with, not just resources a user has access to like delegated permissions. This is because there is no user present in this interaction with the API. You won’t be able to interact with resources until admin consent is granted.
Authentication with a client secret
Now we’ll look at an overview to achieving authentication when we’re using an app to make application only calls. In this case if we’re working with something like Power Automate we’ll use a client secret to authenticate.
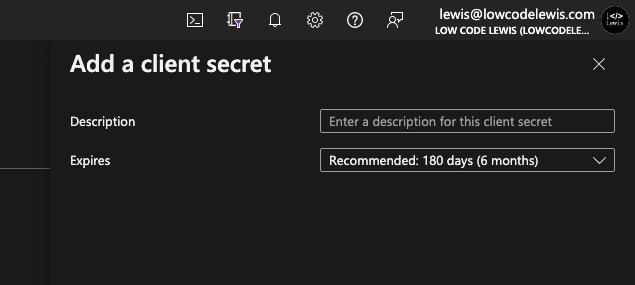
To create a client secret to use for authentication we’ll need to go to the certificates and secrets tab, select client secrets and then simply select new client secret.
Give your secret a description as to what you’ll be using it for, for example where you’re using it to authenticate using the app. Then give it an expiry period and select add.
Once you’ve done that, copy the value that your secret provides from the value field on the data grid/list, then paste this into the place you’re attempting to call the API from within the authentication options.
Upcoming content
In my next blog posts we’ll look specifically at how to use application permissions to interact with Microsoft Graph in 1. a Power Automate flow and 2. Power Apps.
Make sure you’re subscribed to my blog to get my continued upcoming content on Microsoft Graph and utilising the wider Microsoft Cloud ecosystem to deliver better, more impactful low code solutions with contextual data.

