Want to ensure you don’t become that second person in your organisation managing access to the 5 Power Platform solutions you just developed, with this kinda practice continuing for each next solution you build? Nope people! Don’t do this! 👎 🚫
In this post, we’ll look at how you can avoid this by using Microsoft Entra security groups as Teams in Power Platform to hand the responsibility of providing access to things i.e. Teams, up to your central IT team who manage these security groups!
Entra ID Security Group
So, to begin with, I have a Microsoft Entra ID security group, which I’d like to use to control the membership of a team in Dataverse with which will then get assigned security roles to control access to things.
Configuration in Dataverse
Now let’s look at how we configure a Dataverse team to utilise the membership of our security group now. In this environment I’m going to start by creating a new team, which I’ll select the type as ‘Microsoft Entra ID Security Group’ for. Then from here I can search for and select the group that I want to use to control the membership of this team with. Effectively we have two groups in sync here and we’re using using a security group in Dataverse and assigning it roles and access/ownership to data.
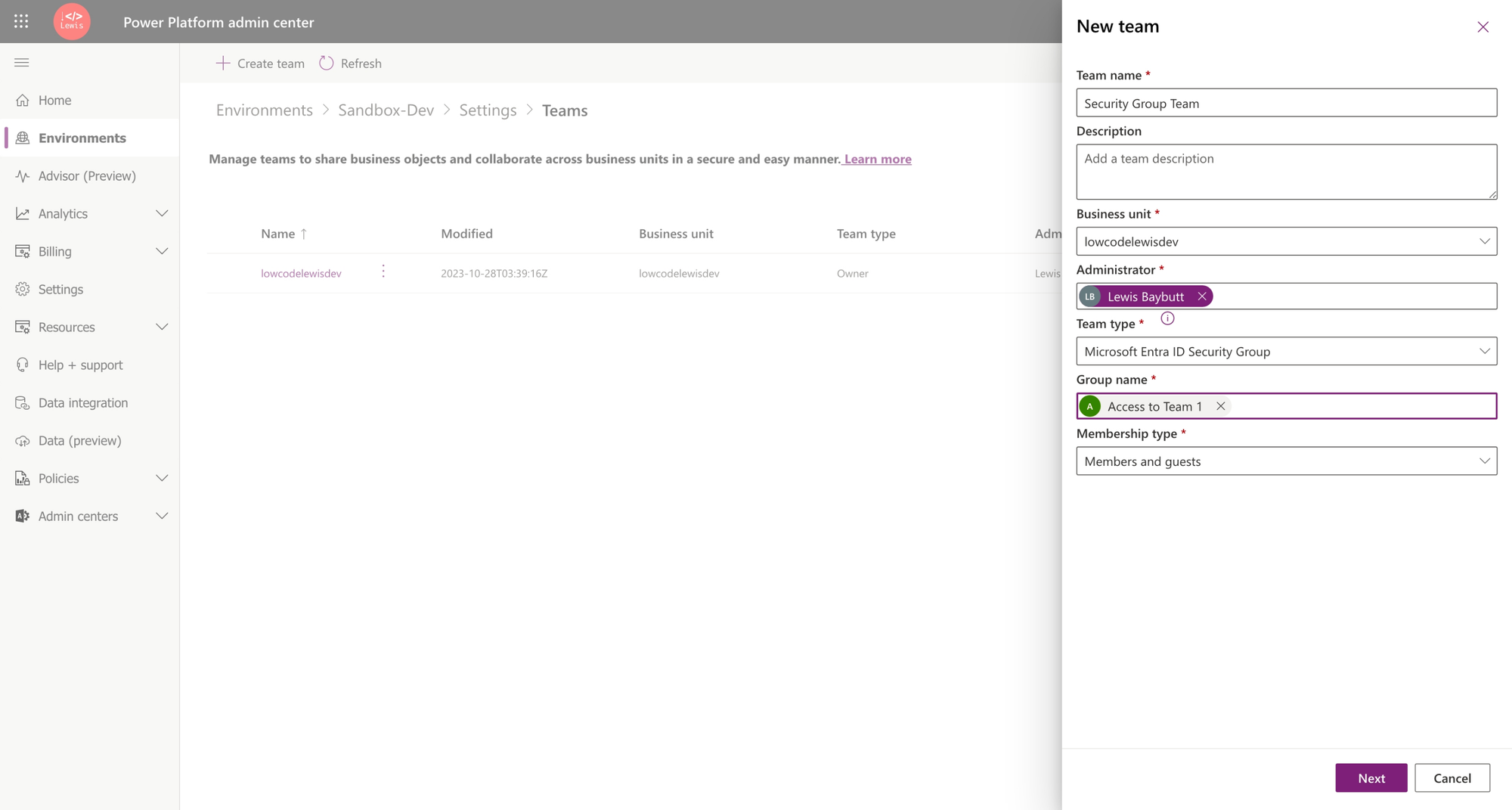
From here add relevant roles to the team.

Now, anyone you add to that security group in Microsoft Entra ID, will have the roles you just applied, applied to them via the team they are a part of, and will get access to those relevant resources! Simples! 🚀
